HashiCorp joins IBM to accelerate the mission of multi-cloud automation and bring the products to a broader audience of users and customers.
Today we announced that HashiCorp has signed an agreement to be acquired by IBM to accelerate the multi-cloud automation journey we started almost 12 years ago. I’m hugely excited by this announcement and believe this is an opportunity to further the HashiCorp mission and to expand to a much broader audience with the support of IBM.
When we started the company in 2012, the cloud landscape was very different than today. Mitchell and I were first exposed to public clouds as hobbyists, experimenting with startup ideas, and later as professional developers building mission-critical applications. That experience made it clear that automation was absolutely necessary for cloud infrastructure to be managed at scale. The transformative impact of the public cloud also made it clear that we would inevitably live in a multi-cloud world. Lastly, it was clear that adoption of this technology would be driven by our fellow practitioners who were reimagining the infrastructure landscape.
We founded HashiCorp with a mission to enable cloud automation in a multi-cloud world for a community of practitioners. Today, I’m incredibly proud of everything that we have achieved together. Our products are downloaded hundreds of millions of times each year by our passionate community of users. Each year, we certify tens of thousands of new users on our products, who use our tools each and every day to manage their applications and infrastructure.
We’ve partnered with thousands of customers, including hundreds of the largest organizations in the world, to power their journey to multi-cloud. They have trusted us with their mission-critical applications and core infrastructure. One of the most rewarding aspects of infrastructure is quietly underpinning incredible applications around the world. We are proud to enable millions of players to game together, deliver loyalty points for ordering coffee, connect self-driving cars, and secure trillions of dollars of transactions daily. This is why we’ve always believed that infrastructure enables innovation.
The HashiCorp portfolio of products has grown significantly since we started the company. We’ve continued to work with our community and customers to identify their challenges in adopting multi-cloud infrastructure and transitioning to zero trust approaches to security. These challenges have in turn become opportunities for us to build new products and services on top of the HashiCorp Cloud Platform.
This brings us to why I’m excited about today's announcement. We will continue to build products and services as HashiCorp, and will operate as a division inside IBM Software. By joining IBM, HashiCorp products can be made available to a much larger audience, enabling us to serve many more users and customers. For our customers and partners, this combination will enable us to go further than as a standalone company.
The community around HashiCorp is what has enabled our success. We will continue to be deeply invested in the community of users and partners who work with HashiCorp today. Further, through the scale of the IBM and Red Hat communities, we plan to significantly broaden our reach and impact.
While we are more than a decade into HashiCorp, we believe we are still in the early stages of cloud adoption. With IBM, we have the opportunity to help more customers get there faster, to accelerate our product innovation, and to continue to grow our practitioner community.
I’m deeply appreciative of the support of our users, customers, employees, and partners. It has been an incredibly rewarding journey to build HashiCorp to this point, and I’m looking forward to this next chapter.
Additional Information and Where to Find It
HashiCorp, Inc. (“HashiCorp”), the members of HashiCorp’s board of directors and certain of HashiCorp’s executive officers are participants in the solicitation of proxies from stockholders in connection with the pending acquisition of HashiCorp (the “Transaction”). HashiCorp plans to file a proxy statement (the “Transaction Proxy Statement”) with the Securities and Exchange Commission (the “SEC”) in connection with the solicitation of proxies to approve the Transaction. David McJannet, Armon Dadgar, Susan St. Ledger, Todd Ford, David Henshall, Glenn Solomon and Sigal Zarmi, all of whom are members of HashiCorp’s board of directors, and Navam Welihinda, HashiCorp’s chief financial officer, are participants in HashiCorp’s solicitation. Information regarding such participants, including their direct or indirect interests, by security holdings or otherwise, will be included in the Transaction Proxy Statement and other relevant documents to be filed with the SEC in connection with the Transaction. Additional information about such participants is available under the captions “Board of Directors and Corporate Governance,” “Executive Officers” and “Security Ownership of Certain Beneficial Owners and Management” in HashiCorp’s definitive proxy statement in connection with its 2023 Annual Meeting of Stockholders (the “2023 Proxy Statement”), which was filed with the SEC on May 17, 2023 (and is available at https://www.sec.gov/ix?doc=/Archives/edgar/data/1720671/000114036123025250/ny20008192x1_def14a.htm). To the extent that holdings of HashiCorp’s securities have changed since the amounts printed in the 2023 Proxy Statement, such changes have been or will be reflected on Statements of Change in Ownership on Form 4 filed with the SEC (which are available at https://www.sec.gov/cgi-bin/browse-edgar?action=getcompany&CIK=0001720671&type=&dateb=&owner=only&count=40&search_text=). Information regarding HashiCorp’s transactions with related persons is set forth under the caption “Related Person Transactions” in the 2023 Proxy Statement. Certain illustrative information regarding the payments to that may be owed, and the circumstances in which they may be owed, to HashiCorp’s named executive officers in a change of control of HashiCorp is set forth under the caption “Executive Compensation—Potential Payments upon Termination or Change in Control” in the 2023 Proxy Statement. With respect to Ms. St. Ledger, certain of such illustrative information is contained in the Current Report on Form 8-K filed with the SEC on June 7, 2023 (and is available at https://www.sec.gov/ix?doc=/Archives/edgar/data/1720671/000162828023021270/hcp-20230607.htm).
Promptly after filing the definitive Transaction Proxy Statement with the SEC, HashiCorp will mail the definitive Transaction Proxy Statement and a WHITE proxy card to each stockholder entitled to vote at the special meeting to consider the Transaction. STOCKHOLDERS ARE URGED TO READ THE TRANSACTION PROXY STATEMENT (INCLUDING ANY AMENDMENTS OR SUPPLEMENTS THERETO) AND ANY OTHER RELEVANT DOCUMENTS THAT HASHICORP WILL FILE WITH THE SEC WHEN THEY BECOME AVAILABLE BECAUSE THEY WILL CONTAIN IMPORTANT INFORMATION. Stockholders may obtain, free of charge, the preliminary and definitive versions of the Transaction Proxy Statement, any amendments or supplements thereto, and any other relevant documents filed by HashiCorp with the SEC in connection with the Transaction at the SEC’s website (http://www.sec.gov). Copies of HashiCorp’s definitive Transaction Proxy Statement, any amendments or supplements thereto, and any other relevant documents filed by HashiCorp with the SEC in connection with the Transaction will also be available, free of charge, at HashiCorp’s investor relations website (https://ir.hashicorp.com/), or by emailing HashiCorp’s investor relations department ([email protected]).
Forward-Looking Statements
This communication may contain forward-looking statements that involve risks and uncertainties, including statements regarding (i) the Transaction; (ii) the expected timing of the closing of the Transaction; (iii) considerations taken into account in approving and entering into the Transaction; and (iv) expectations for HashiCorp following the closing of the Transaction. There can be no assurance that the Transaction will be consummated. Risks and uncertainties that could cause actual results to differ materially from those indicated in the forward-looking statements, in addition to those identified above, include: (i) the possibility that the conditions to the closing of the Transaction are not satisfied, including the risk that required approvals from HashiCorp’s stockholders for the Transaction or required regulatory approvals to consummate the Transaction are not obtained, on a timely basis or at all; (ii) the occurrence of any event, change or other circumstance that could give rise to a right to terminate the Transaction, including in circumstances requiring HashiCorp to pay a termination fee; (iii) possible disruption related to the Transaction to HashiCorp’s current plans, operations and business relationships, including through the loss of customers and employees; (iv) the amount of the costs, fees, expenses and other charges incurred by HashiCorp related to the Transaction; (v) the risk that HashiCorp’s stock price may fluctuate during the pendency of the Transaction and may decline if the Transaction is not completed; (vi) the diversion of HashiCorp management’s time and attention from ongoing business operations and opportunities; (vii) the response of competitors and other market participants to the Transaction; (viii) potential litigation relating to the Transaction; (ix) uncertainty as to timing of completion of the Transaction and the ability of each party to consummate the Transaction; and (x) other risks and uncertainties detailed in the periodic reports that HashiCorp files with the SEC, including HashiCorp’s Annual Report on Form 10-K. All forward-looking statements in this communication are based on information available to HashiCorp as of the date of this communication, and, except as required by law, HashiCorp does not assume any obligation to update the forward-looking statements provided to reflect events that occur or circumstances that exist after the date on which they were made.
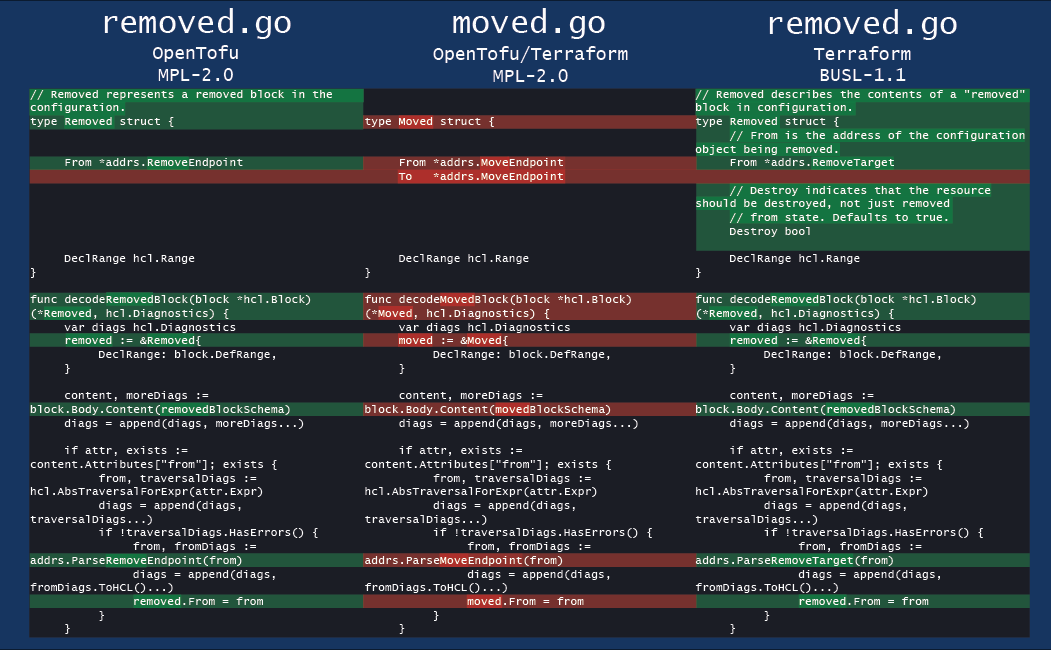
RIP Hashicorp, any good alternatives? Use most of their stack.


I'm aware that this isn't how DNS works, but I'd imagine it is possible to have a DNS server that when it receives a query from the internet looks at the requested domain and translates it to an internal domain and in turn query that one, returning the result without revealing the internal domain. Something like a ALIAS virtual record provided by some services (but wont work against a internal DNS).
As for Traefik acting as a reverse proxy for internal network addresses, yeah that's the way it works. However in this case I have several instances of Traefik running on a subset of IP-addresses on a public subnet. So essentially we want to loadbalance several Traefik loadbalancers using DNS.