I found a few links summarising this:
- https://old.reddit.com/r/nextdns/comments/14919dp/randomly_pathnxtracloudnet_is_stopped_getting/jo5n5va/
-
It's Qualcomm's URL for downloading assisted GPS almanac days
-
- https://teddit.net/r/privacy/comments/12yii9u/comment/jhojlr7/
- Graphene OS' relevant documentation: https://grapheneos.org/faq#default-connections
On 4th and 5th generation Pixels (which use a Qualcomm baseband providing cellular, Wi-Fi, Bluetooth and GNSS in separate sandboxes), almanacs are downloaded from
https://qualcomm.psds.grapheneos.org/xtra3Mgrbeji.binwhich is a cache of Qualcomm's data. Alternatively, the standard servers can be enabled in the Settings app which will usehttps://path1.xtracloud.net/xtra3Mgrbeji.bin,https://path2.xtracloud.net/xtra3Mgrbeji.binandhttps://path3.xtracloud.net/xtra3Mgrbeji.bin. GrapheneOS improves the privacy of Qualcomm PSDS (XTRA) by removing the User-Agent header normally containing an SoC serial number (unique hardware identifier), random ID and information on the phone including manufacturer, brand and model. We also always fetch the most complete XTRA database variant (xtra3Mgrbeji.bin) instead of model/carrier/region dependent variants to avoid leaking a small amount of information based on the database variant.
Note sure if e/OS/ has taken as much care as Graphene has to make the requests more private. Then again, they don't claim to be the most private OS, just De-Googled.
Edit: this is also a good read for further attempts to make your device more private: https://grapheneos.org/faq#other-connections

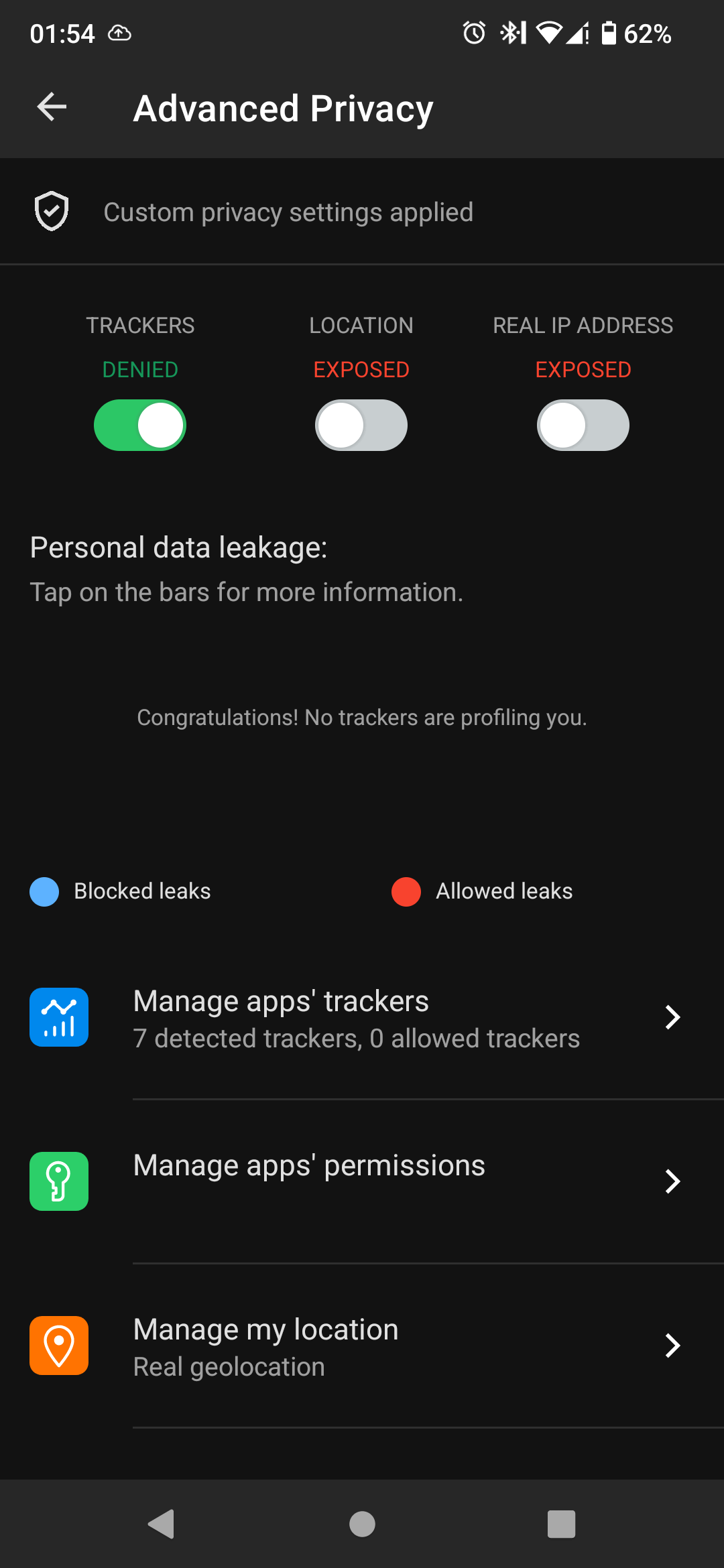
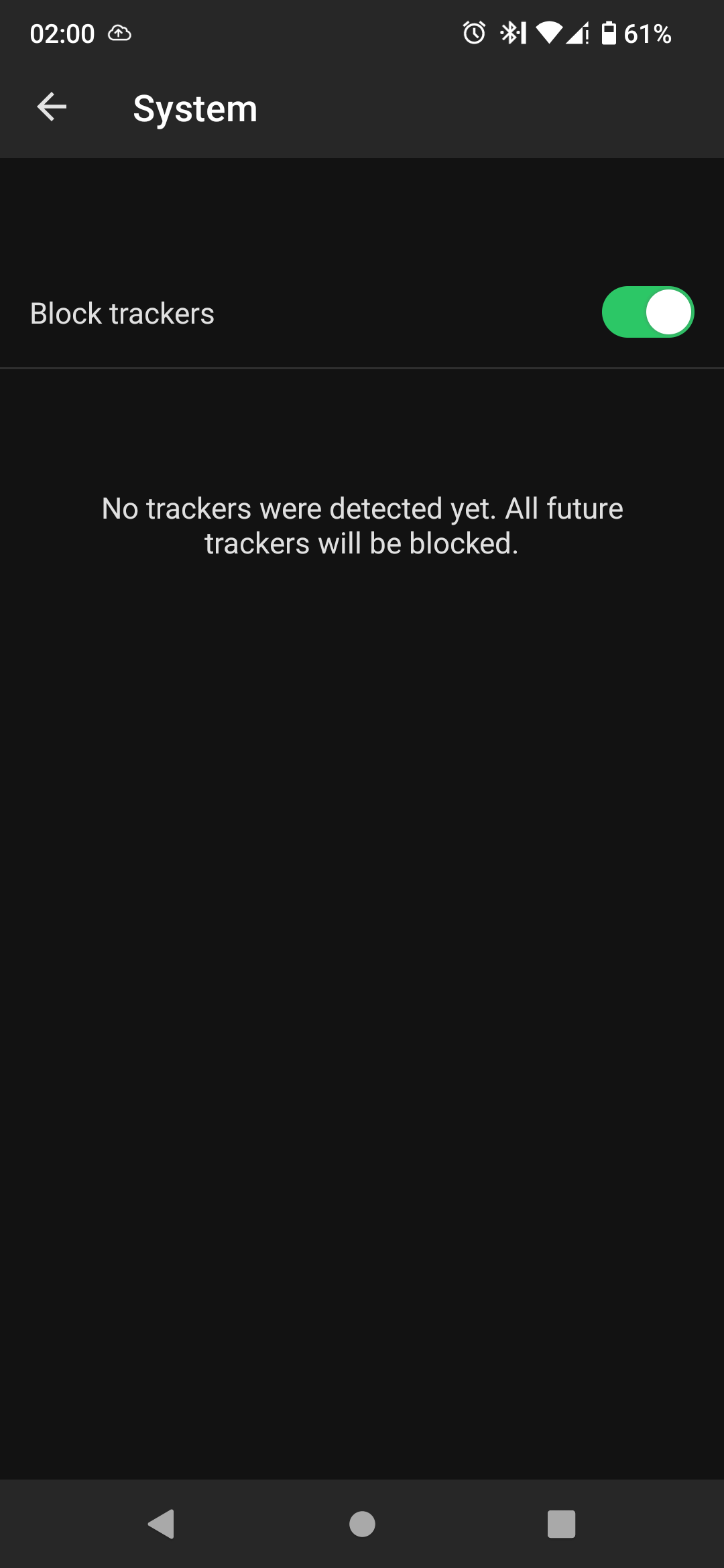
 I am guesing that because dns is blocking the requests they dont show in the app.
That would mean the app and dns are doing the same thing, so it doesnt really help.
I am guesing that because dns is blocking the requests they dont show in the app.
That would mean the app and dns are doing the same thing, so it doesnt really help.