You're welcome, I am here for the community 👍
One of the Proton Linux devs just commented about that over in the Proton VPN subreddit:
We're going to work on it, there are some issues with the DNS resolver that debian uses, which is not the same as Ubuntu and Fedora, which makes split tunneling behave in an unexpected manner.
Out of curiosity, are you or any of the other mods with Proton officially? I appreciate the updates regardless, I was curious if this was an official / unofficial community
We are the same volunteering moderators as on all the Proton subreddits. Official in that way and that the owner of the board here is the Proton account beloging to the team, unofficial in the way that the Proton Team isn't really present here.
Do you still need help or did you get it sorted?
Apple officially allows and supports VPN apps since tvOS 17 and there are many VPN apps available for Apple TV now.
For those asking about Stealth on Linux, quote from the team:
With Wireguard for Linux about to come out of beta and we are planning to bring Stealth to Linux as well.
The team states the following regarding Firefox:
Support for running language models locally is currently only available in the Firefox Nightly builds. In our testing with Firefox, we haven’t been able to get Proton Scribe to run reliably on a variety of devices. We will see how the situation evolves before adding support.
Just a note to add, this is just the re-confirmation of this year, the two previous years they have had no-logs policy audits as well :)
Different teams, different products. One thing doesn't exclude the other.
The team is already on it.
All password managers keep data unencrypted in memory. You can't encrypt the data in memory because then the application cannot use the data while it is running. It's an universal issue for password managers, and not something that can be fixed.
While you can obfuscate the data, this is really security theater, because it is trivial to reverse engineer the obfuscation. In the future, Proton Pass may also obfuscate, but it doesn't actually add any security.
If you enable PIN lock, the data is encrypted locally and cleared from memory when the PIN lock is activated. The security benefit of this in the case of a compromised device is likely marginal, as malware on a device would be able to key log the pin and bypass it in that manner. However, PIN lock can be desirable on a shared device (although somebody with access to the shared device could also install a keylogger...).
In the previous version of Proton Pass, after the PIN lock, it can take up to 30 minutes to clear data from memory, while the new version clears it immediately. It was previously immediate, but a code regression set it back to up to 30 minutes, but this has now been fixed. In general, for the reasons previously explained, we would not advise people to rely upon the PIN to secure against malware or shared devices, and that's why PIN is not enabled by default, as the security benefit is likely marginal.
By the way, to even take advantage of this, somebody would need to have access to the device and the ability to access the device memory, in which case the PIN is not going to be effective because the device is already compromised. Unfortunately protecting against this type of device compromise is beyond the scope of Proton Pass (or any other password manager).
The most important part is highlighted in bold.
Source:




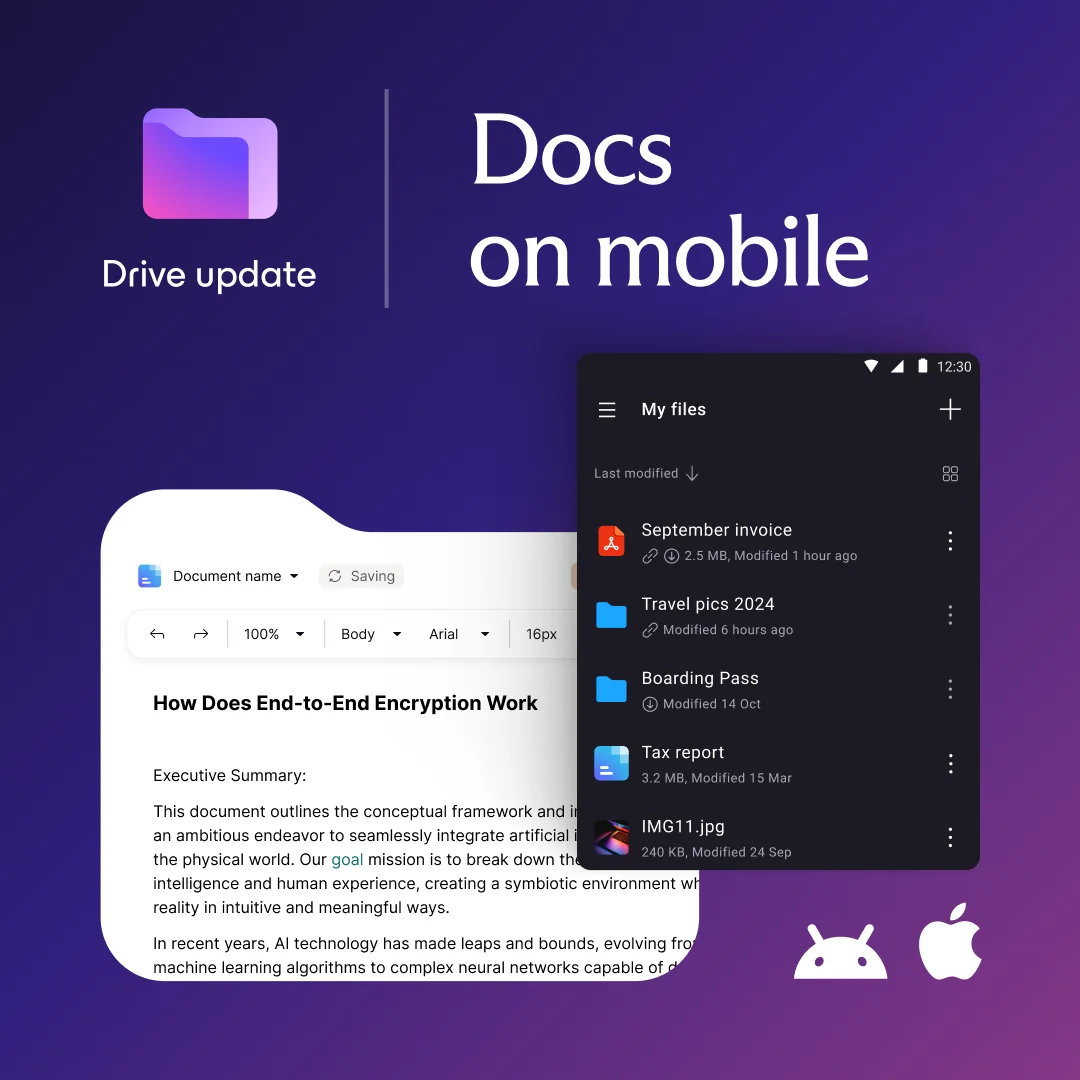
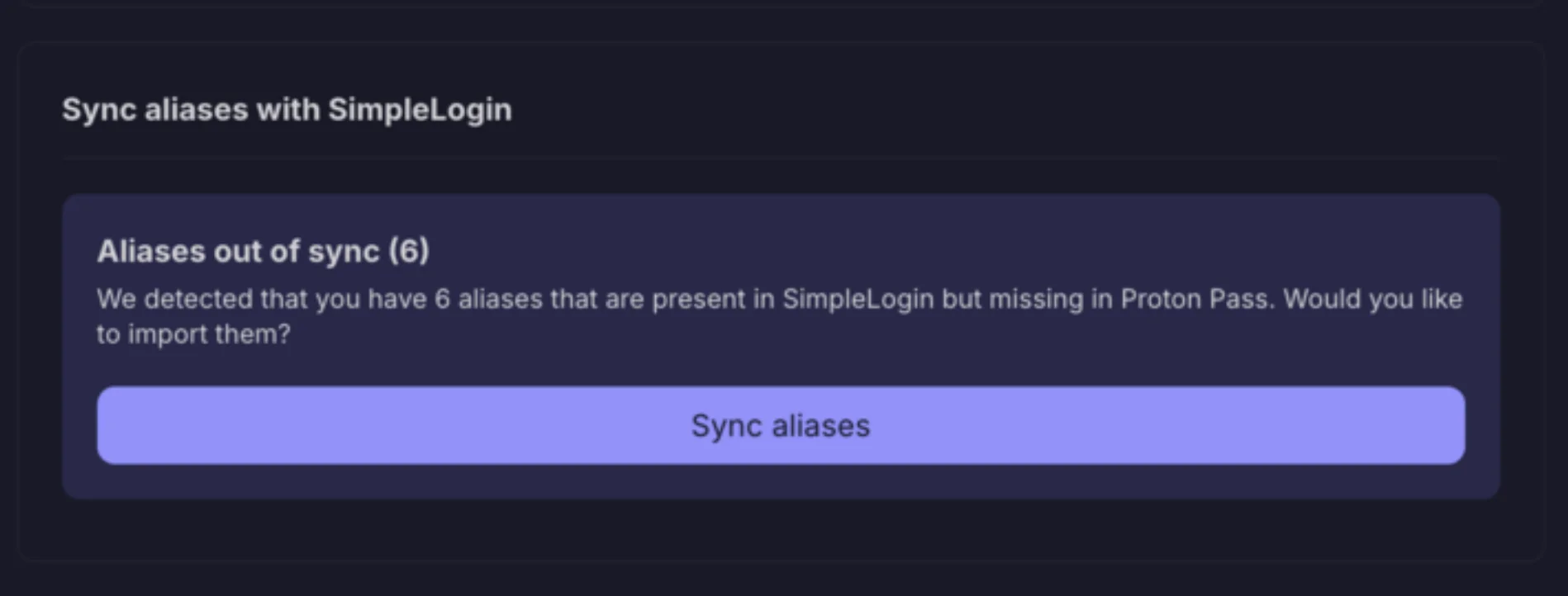
Still planned for summer, which in Switzerland (HQ of Proton) is until 22nd September